Securing connected Power and Cooling assets
Your telecommunication sites and data centers are under mounting pressure to provide rapid, scalable, secure, and more efficient business operations. They must accommodate ever-increasing network elements, computing and data volume, ever-changing security and technological requirements, and the need to maintain dependable service levels.
We sometimes forget that critical power and cooling assets deployed in these buildings are the backbones of your business operations. The proliferation of network elements and IT equipment stresses the power and cooling density and can lead to unexpected problems such as overheating, overloads, lack of capacity, or even loss of redundancy. The ability to measure, monitor, and control power and cooling assets combined with capacity management software is the best way to ensure an optimized usage of power and cooling assets, forecast power and cooling demands while lowering your Total Cost of Ownership (TCO).
One thing today’s power and cooling assets all have in common is that they all have the ability to be connected on your corporate network, meaning they can be accessed remotely. However, one thing they do not have in common, is their level of compliance with today’s evolving network security policies. As more and more users need access to power and cooling assets data, there must be a way to identify and restrict who is allowed on the network and what access they are granted for each asset type.
Critical connected power and cooling assets
Power and cooling assets consist of several components each having a smart controller that all play an essential role in monitoring and controlling power and environmental operating conditions. Therefore, securing critical connected power and cooling assets is of utmost importance to your business continuity and efficiency.
The National Institute of Standards and Technology (NIST) defines criticality in terms of the impact of the “function or component failure on the ability of the component [system] to complete the organizational missions supported by the information system.”[1]
Typical connected Power Devices
- Uninterruptible Power Supply (UPS)
- DC Power System Controller
- Battery Monitoring System
- Smart Battery Charger
- Smart Inverters or Smart Converters
- Intelligent Power Distribution Strips
- Branch Circuit Monitoring devices
- Generator Controller
- Fuel System Management
- Automatic Transfer Switch
- Surge Protective Devices
- Programmable Logic Controller (PLC)
- Energy or Power Meters
Typical connected Cooling Devices
- Rooftop HVAC Systems (RTU)
- Heat Pumps and Glycol Pumps
- Building Automation Systems (BAS)
- Programmable Logic Controllers (PLC)
- Computer Room Air Conditioner (CRAC)
- Computer Room Air Handling (CRAH)
- Air Handling Units (AHU)
- Remote Telemetry Unit (RTU)
- Chilled Water Plant
- Heat Exchanger
- Intelligent thermostat
- Air Terminal Unit
How many of these connected assets are designed for network security?
Connected power and cooling devices are not really designed with network security in mind at all. If you operate a railway network, data center, telecom network or you are in the electrical power utility sector, you have legacy power and cooling assets connected on your network without a doubt. These legacy devices were simply designed to function and chances are they provide a TCP/IP connection for remote access purposes and some may have an open standard protocol such as SNMP, for sending alarms to your fault management platform at the Network Operating Center (NOC). More recent power and cooling devices will offer an embedded web server with little to no network security protocols or means for authentication, unless they have a login requesting a user name and password which is most of the time configured with “ADMIN” and “ADMIN” respectively. The IT department ensures the network security and governance of applications, services, and IT network infrastructure.
Until fairly recently, businesses were kept reasonably protected relative to how exposed they are, but that’s changing very fast. For many of you, the IT department has started pulling the plug on connected power and cooling devices that are not compliant with the minimum corporate network security policies. Thus, you are being forced to mitigate the situation, which can involve the following possibilities:
1. Deploying a managed IP switch with DHCP
The switch will segregate your connected power and cooling devices from the network; However, the deployment of IT infrastructure is not part of your mandate, thus it falls under the responsibility of the IT department and they will not endorse this strategy as it is just an extension of the current network.
2. Disconnecting the connected devices from the network
This is truly not what we are looking for as it leaves you and your peers without critical data from the power or cooling assets. Losing remote visibility of these critical assets is counterintuitive to becoming more efficient and performant in your work.
3. Replacing the unsecured connected devices with secured compliant devices
In today’s reality, it is not as easy as it sounds, power and cooling assets are ecosystems where all sub-components are monitored and controlled by the connected device which is in most cases, not vendor agnostics. Meaning, that the connected device will only operate with its own make and model sub-components. Thus, an unsecured connected device replacement turns into a major power and cooling asset replacement project. Therefore, if the asset to be replaced is obsolete but still functional and efficient, it may not be a good idea to do so. However, if the asset is due and budgeted for replacement and the new asset is more energy efficient, mostly the justification is there (Return on Investment) to proceed.
4. Uploading new firmware onto the non-secure devices
For this to happen, the firmware update must exist and made available. The firmware will need to be qualified to comply with corporate network security policies. Firmware updates are not trivial, they come with a risk of failure, which can lead to service interruptions. Some firmware update procedures require implication of costly on-site human resources and lastly, the firmware updates themself can be expensive, they can range between 0$ up to 2500$ per device.
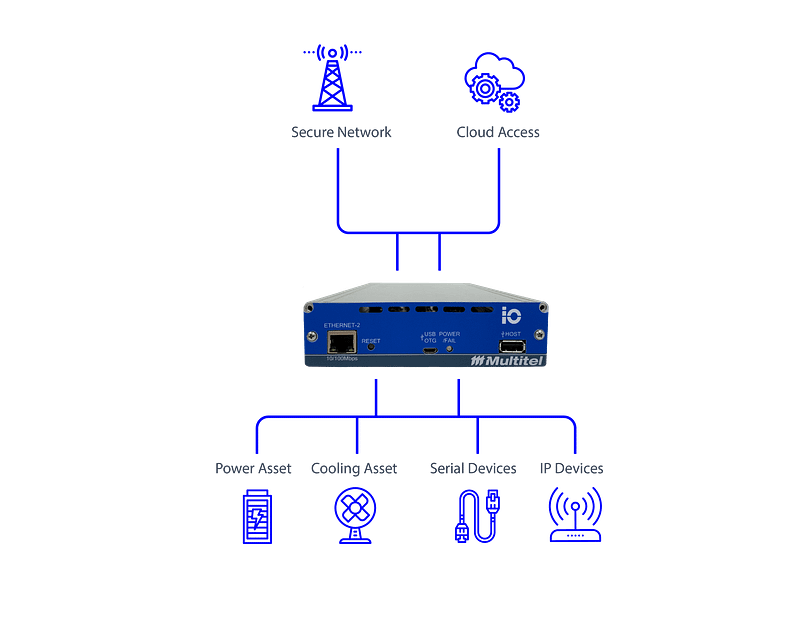
5. Installing Multitel’s all-in-one secure power and cooling asset gateway
Recently, Multitel introduced the iO Gateway with built-in LDAP (Lightweight Directory Access Protocol). The LDAP protocol will enable you to authenticate users wanting to connect to power and cooling devices by assigning them a level of access based on their credentials. Thus, the iO Gateway allows you to setup and maintain your own secured remote access single-site LAN without the cost of VPN subscription fees.
The connected power and cooling devices are bridged to an unmanaged LAN switch and are assigned an IP address from the LAN subnet. The authenticated users will have access to the same experience as if they were connected directly to the power and cooling device’s web servers due to Multitel’s exclusive passthrough feature. Unsecured power and cooling devices will then be manageable using secure SNMP v3 protocols. In summary, the following network security features are made possible only with the iO Gateway:
- Adds SSL layer to connected power and cooling device’s HTTP interface (HTTPS Passthrough);
- Users centralized authentication with your Network Active Directory (LDAP);
- Turns SNMP v1/v2c devices into secure SNMP v3 management;
- Eliminate the need for network IP address management for all your power and cooling assets;
In addition, the iO Gateway can accelerate your data-driven transformation by providing protocol conversion for Modbus power and cooling devices. Meaning you can translate Modbus RTU or Modbus TCP to secure SNMP v3. This opens the door to extract data from Modbus power and cooling devices you had never though possible in a unified, structured and secured manner.
Multitel’s iO Gateway will not only help secure todays and legacy’s connected power and cooling assets, it will eliminate the need for new network IP addresses which are becoming a scarce resource. The iO Gateway is the ideal solution to comply with increasing network security policies while maintaining remote visibility and remote access to your critical power and cooling asset data.
In summary, network connection is not trivial, one must protect it at all costs as it provides remote access and remote visibility to a wealth of information and possibilities that drive:
- Operational efficiency;
- Prevents downtime;
- Reduces energy consumption;
- Extends asset lifecycle;
- Reduces greenhouse gases and sustainability impact.